Your backup strategy just became obsolete overnight.
While you've been focusing on recovery plans and 3-2-1 backup rules, ransomware groups quietly shifted their entire playbook. They're not just encrypting your files anymore, they're stealing everything valuable first, then holding both your operations AND your reputation hostage.
The latest insurance data shows double extortion tactics now account for nearly half of all ransomware claims, and here's the kicker: having perfect backups won't save you from the worst part of these attacks.
What Makes Double Extortion Different (And Why It's Winning)
Traditional ransomware was straightforward, hackers encrypted your files and demanded payment for the decryption key. If you had solid backups, you could essentially tell them to take a hike and restore everything yourself.
Double extortion flipped that script completely.
Now, attackers spend weeks inside your network first, quietly copying your most sensitive data, customer records, financial information, trade secrets, employee details, everything that would hurt if it went public. Only after they've stolen what they want do they encrypt your systems and make their demands.
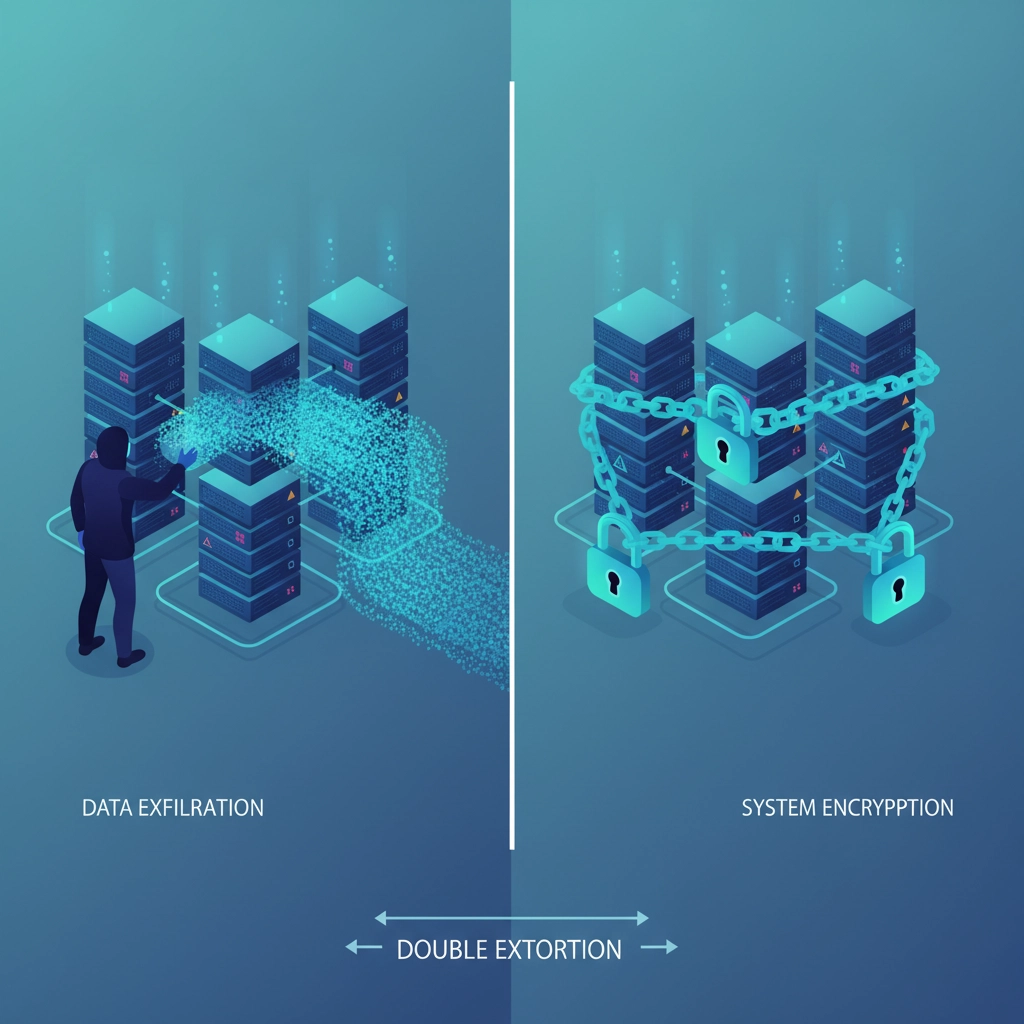
Their ransom note now comes with two threats: "Pay up, or we'll never give you the decryption keys AND we'll leak all your stolen data on the dark web for everyone to see."
This isn't theoretical. In 2024, double extortion comprised 70% of all ransomware attacks, and the numbers keep climbing. Attackers discovered that businesses pay 340% higher ransoms when their reputation is also on the line, not just their operational recovery.
The genius (from a criminal perspective) is that your backup strategy becomes almost irrelevant. Sure, you can restore your encrypted files from backups and get back to business. But you still can't un-steal the data that's already been copied. The threat of public exposure and regulatory penalties often becomes more terrifying than the operational downtime.
Why Your Current Backup Strategy Won't Stop Data Theft
Here's the uncomfortable truth: backups solve the wrong half of the double extortion problem.
Think about it this way: if someone breaks into your house, takes photos of all your personal documents, then burns down the house, having house insurance doesn't help with the blackmail part. You can rebuild the house, but those photos are still out there.
That's exactly what's happening with ransomware now. Groups like Play, LockBit, and dozens of others have refined their data theft techniques to the point where they can exfiltrate terabytes of information without triggering most security systems. They know exactly what to look for: databases, financial records, customer information, anything that would cause regulatory or reputational damage if leaked.

The FBI recently tracked around 900 entities impacted by just the Play ransomware group alone, and in most cases, the organizations had functioning backups. It didn't matter. The stolen data still gave attackers all the leverage they needed.
Even worse, some newer attacks skip encryption entirely. Recent data shows 6% of ransomware attacks in 2025 involved pure extortion without any file encryption: double the rate from 2024. They're just stealing data and threatening to leak it, because that's often enough to get paid.
Your backup strategy isn't useless, but it's solving yesterday's problem while today's criminals have already moved on to tomorrow's tactics.
The 3-Layer Defense Framework That Actually Works
Stopping double extortion requires thinking beyond recovery to prevention and detection. Here's the defense framework that actually matches how these attacks work:
Layer 1: Prevent Data Theft Before It Happens
Network Segmentation becomes your first line of defense. Instead of letting attackers roam freely through your entire network once they're inside, segment your infrastructure so that compromising one system doesn't automatically give access to everything else.
Most businesses run their networks like a big open warehouse: once you're inside, you can access anything. Segmentation is like adding locked doors between different areas, so even if attackers get through the front door, they can't easily reach your most valuable data.
Data Loss Prevention (DLP) tools monitor and block unauthorized data transfers. These systems watch for unusual data movement: like someone trying to copy your entire customer database at 3 AM: and can automatically block or alert on suspicious activity before terabytes of information leave your network.
Rigorous patch management eliminates the vulnerabilities attackers use to get inside in the first place. This isn't just "install updates when convenient": it's maintaining a formal schedule and prioritizing security patches that could prevent initial compromise.
Layer 2: Build Resilience Through Smart Backup Strategy
Your backup approach needs to evolve beyond basic recovery to account for extended investigation and remediation periods.
The 3-2-1 backup rule still applies, but with modern twists: three copies of your data, on two different media types, with one copy stored completely offline and off-site. But now you also need to ensure those backups are tested daily and verified malware-free.

Immutable storage solutions prevent attackers from corrupting your backups even if they find them. Unlike regular backups that can be encrypted or deleted, immutable storage creates permanent, unmodifiable copies that serve as your ultimate safety net.
The key is building enough redundancy that you can refuse to pay ransoms while still maintaining business operations during recovery.
Layer 3: Response and Continuity Planning
Your incident response plan needs to account for both operational recovery AND data breach disclosure requirements.
Tested incident response plans should outline procedures for containment, forensic investigation, and recovery that don't rely on paying ransoms. This includes having relationships with cybersecurity forensic firms established before you need them.
Alternative recovery sites and business continuity measures ensure you can maintain critical operations from backup locations while your primary environment is being investigated and rebuilt.
The goal isn't just to recover: it's to recover while maintaining customer trust and regulatory compliance.
The Current Threat Landscape: What You're Really Up Against
The numbers tell the story: despite law enforcement successes against major groups like LockBit, overall attack volumes remain at historically high levels. There are approximately 65 actively attacking ransomware groups right now, with new ones emerging as others get disrupted.
The average ransom demand in 2024 reached $5.2 million, but here's the encouraging news: payment rates have dropped to around 35% in 2025, down from 85% in 2021. Organizations with strong incident response capabilities are increasingly refusing to pay, which puts more pressure on having solid defense and recovery strategies.

But the criminals are adapting too. They're targeting higher-value organizations, spending more time in networks before striking, and getting better at identifying and stealing the most damaging data. Some groups now offer "data destruction guarantees" for additional payment, recognizing that regulatory compliance concerns often outweigh operational recovery costs.
Taking Action: Your Next Steps
The shift to double extortion means cybersecurity is no longer just an IT problem: it's a business risk management issue that requires executive-level attention and investment.
Start by auditing your current backup and recovery capabilities, but expand that audit to include data loss prevention, network segmentation, and incident response planning. You need to know not just whether you can recover from encryption, but whether you can prevent data theft in the first place and respond appropriately if prevention fails.
Consider your regulatory and compliance obligations under frameworks like NIST CSF 2.0, which provide structured approaches to cybersecurity risk management that account for modern threat techniques.
Most importantly, recognize that this is an ongoing program, not a one-time implementation. The threat landscape continues evolving, and your defenses need to evolve with it.
Ready to Build a Double Extortion-Proof Defense?
Don't wait until you're explaining to customers why their data appeared on a ransomware leak site. The three-layer defense framework isn't theoretical: it's the proven approach that's keeping businesses protected while others pay millions in ransoms.
At B&R Computers, we help businesses implement comprehensive ransomware defense strategies that account for modern double extortion tactics. From network segmentation and DLP implementation to incident response planning and compliance frameworks, we build defenses that match how attacks actually work in 2025.
Schedule your cybersecurity assessment today and discover where your current backup strategy leaves you vulnerable to data theft threats. Because in the age of double extortion, being able to restore your files isn't enough( you need to protect your reputation too.)





































































































