The cybersecurity landscape just shifted overnight. While everyone was focused on protecting themselves from traditional hackers, artificial intelligence quietly weaponized cybercrime in ways we've never seen before. And the primary victims? Small and medium-sized businesses that thought they were too small to be worth targeting.
Here's the wake-up call: AI-powered cyberattacks increased by 47% globally in just the first half of 2025, with small businesses bearing the brunt of this digital assault. The numbers are staggering: and they're getting worse every month.
Why Small Businesses Became Cybercriminals' Favorite Target
The shift happened fast, but the reasons are crystal clear. Small businesses represent the perfect storm of vulnerability and value for AI-driven attackers.
You're High-Value, Low-Security Targets
SMBs process millions in transactions, store valuable customer data, and maintain direct relationships with larger enterprises: making you incredibly attractive targets. Yet most small businesses operate with skeleton IT crews and security budgets that wouldn't cover a single enterprise security tool.
AI Made Attacks Scalable
What used to require skilled hackers working manually can now be automated across thousands of targets simultaneously. AI doesn't need coffee breaks, doesn't make typos in phishing emails, and can adapt its approach in real-time based on your responses.
The Numbers Don't Lie
Recent data shows that 79% of small businesses experienced at least one cyberattack in the past five years, and here's the kicker: 60% of small businesses that suffer a major cyberattack shut down within six months. The financial reality is brutal: the average cost per breach for SMBs hit $5.72 million in 2025.

Real AI-Powered Attacks Hitting Small Businesses Right Now
Let me share some real examples that happened just in the past few months, because this isn't theoretical anymore.
Voice Cloning Wire Fraud
A Connecticut accounting firm lost $340,000 in March when attackers used AI to clone their CEO's voice. The fake CEO called the finance manager, requested an "urgent" wire transfer for a "confidential acquisition," and provided all the right account details. The voice was so convincing that the finance manager didn't question it until the real CEO walked into the office an hour later.
Adaptive Phishing Campaigns
AI is now personalizing phishing emails in real-time based on your social media activity, recent purchases, and even the weather in your area. A Florida law firm received emails that mentioned their recent case wins, referenced local restaurant reservations from partner LinkedIn posts, and used writing styles that matched their internal communications. Three employees clicked malicious links before IT caught it.
Automated Ransomware Distribution
AI systems are now scanning for vulnerabilities, deploying customized ransomware payloads, and even negotiating ransom payments: all without human involvement. A Michigan manufacturing company discovered their entire network encrypted with a ransom note that addressed them by name and referenced specific equipment they'd recently purchased.
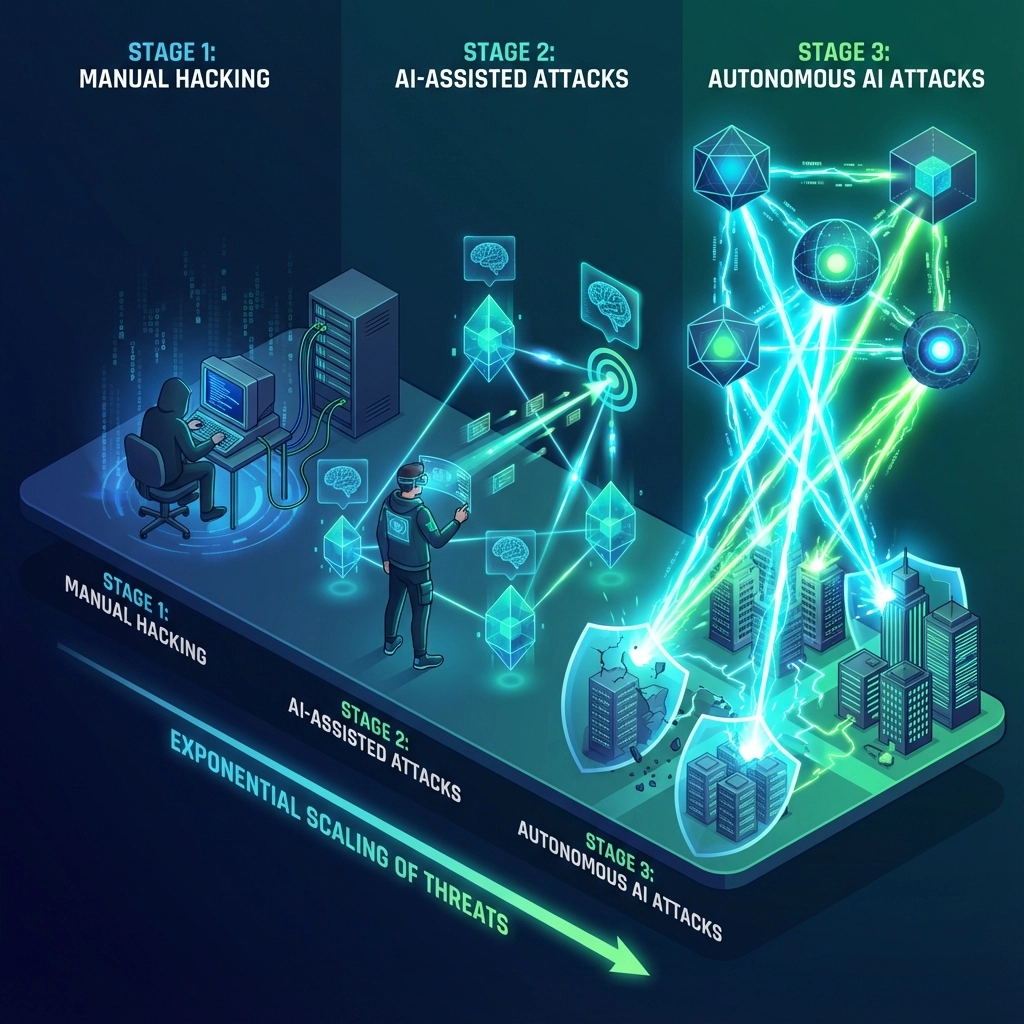
How AI Supercharged Cyberattacks
The technology shift is fundamental. AI isn't just making existing attacks better: it's creating entirely new attack vectors.
Speed and Scale
Traditional attacks required weeks of reconnaissance. AI-powered attacks can scan your entire digital footprint, identify vulnerabilities, and launch targeted campaigns in hours. One AI system can simultaneously manage attacks against hundreds of businesses.
Adaptive Intelligence
When you block one attack vector, AI immediately tries another. It learns from your defenses, adapts its approach, and finds new ways in. It's like having a persistent, never-sleeping attacker who gets smarter with every attempt.
Perfect Impersonation
Voice cloning, deepfake videos, and writing style mimicry have reached the point where they're indistinguishable from the real thing. The "trust but verify" approach doesn't work when verification methods themselves can be compromised.
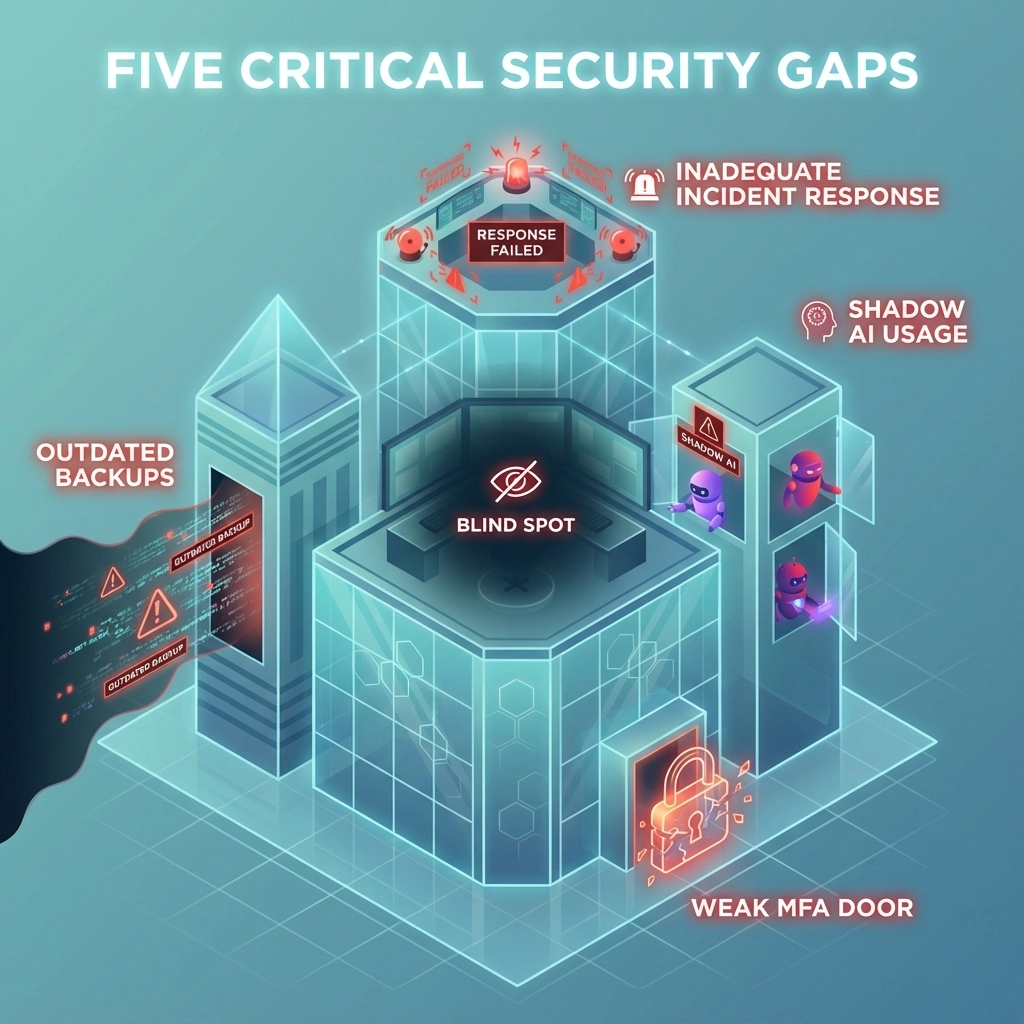
The Five Critical Security Gaps Putting SMBs at Risk
Based on assessments we've conducted this year, here are the five biggest vulnerabilities we see consistently across small businesses:
1. Weak Multi-Factor Authentication (MFA)
The Problem: 73% of SMBs either don't use MFA or use SMS-based MFA, which AI can easily intercept.
The Reality: AI-powered SIM swapping attacks increased by 400% in 2025.
The Fix: Implement app-based or hardware token MFA across all business-critical systems.
2. Outdated Backup Strategies
The Problem: Most SMB backups aren't tested, aren't isolated from networks, and can be encrypted by ransomware.
The Reality: 85% of businesses that pay ransoms don't get all their data back anyway.
The Fix: Follow the 3-2-1-1 rule: 3 backup copies, 2 different media types, 1 offsite, 1 immutable.
3. Shadow AI Usage
The Problem: Employees are using AI tools (ChatGPT, Claude, etc.) for work without IT oversight.
The Reality: Sensitive data shared with AI tools can be accessed by attackers who compromise these platforms.
The Fix: Implement AI governance policies and approved business AI tools.
4. Missing SOC Monitoring
The Problem: SMBs don't have 24/7 security monitoring to detect AI-powered attacks in progress.
The Reality: AI attacks move so fast that standard business-hours monitoring misses 80% of incidents.
The Fix: Implement managed detection and response (MDR) services for continuous monitoring.
5. Inadequate Incident Response Planning
The Problem: When AI-powered attacks hit, most SMBs don't know who to call or what steps to take.
The Reality: Delayed response increases breach costs by 300% and reduces recovery chances significantly.
The Fix: Develop, test, and regularly update an incident response plan with clear escalation procedures.
Your AI-Ready Defense Blueprint
Building effective defenses against AI-powered attacks requires a strategic approach. Here's your practical roadmap:
Phase 1: Immediate Actions (This Week)
- Audit all admin accounts and implement proper MFA
- Update all software and enable automatic security updates
- Review backup systems and test one restore process
- Document all AI tools employees are currently using
Phase 2: Foundation Building (Next 30 Days)
- Conduct a comprehensive risk assessment to identify all vulnerabilities
- Implement network segmentation to limit attack spread
- Deploy endpoint detection on all devices
- Create an incident response playbook with contact information and procedures
Phase 3: Advanced Protection (Next 90 Days)
- Install managed detection and response (MDR) for 24/7 monitoring
- Implement zero-trust network architecture where possible
- Train employees on AI-powered social engineering recognition
- Establish secure AI usage policies and approved tools
Phase 4: Ongoing Optimization
- Monthly security assessments to stay ahead of emerging threats
- Quarterly incident response drills to test your procedures
- Regular employee training updates as attack methods evolve
- Continuous monitoring and improvement of security posture
The Cost of Waiting
Every day you delay implementing these protections, AI-powered attacks are getting more sophisticated. The small business down the street from you might be getting hit right now, and you could be next.
The average SMB cyber insurance claim jumped 40% in 2025, and many insurers are now requiring specific security controls before they'll even provide coverage. Waiting isn't just risky: it's becoming financially impossible.
Take Action Now: Before You Become a Statistic
AI-powered cyberattacks aren't slowing down. They're accelerating, evolving, and specifically targeting businesses just like yours. The question isn't whether you'll be attacked: it's whether you'll be ready when it happens.
Don't wait until you're scrambling to recover from a breach. The businesses surviving these new threats are the ones taking proactive steps to understand their vulnerabilities and fix them before attackers find them.
Ready to see exactly where your business stands against AI-powered threats?
Book a comprehensive Cybersecurity Risk Assessment with B&R Computers. We'll show you precisely which vulnerabilities AI-powered attackers would exploit in your environment, what it would cost your business, and the specific steps to close those gaps before they become problems.
During your assessment, we'll evaluate your current defenses against the exact attack methods we discussed in this article, provide you with a detailed vulnerability report, and give you a clear roadmap to AI-ready cybersecurity: all with no obligation.
Contact B&R Computers today to schedule your risk assessment. Because in 2025, the best defense against AI-powered attacks is knowing your weaknesses before cybercriminals do.





































































































