Remember when getting cyber insurance was as simple as promising you had "good antivirus software"? Those days are officially over. In 2025, cyber insurers have completely flipped the script on what they're willing to cover: and it's all because of one massive problem that's bleeding them dry: ransomware.
If you've been putting off that cyber insurance renewal or shopping around for new coverage, you've probably already felt the sting of these changes. Insurers are now demanding proof of actual security controls, not just promises. And honestly? It's about time.
The Real Ransomware Numbers (Spoiler: They're Worse Than You Think)
While that 60% figure gets thrown around a lot, the actual ransomware statistics paint an even grimmer picture. Here's what's really happening:
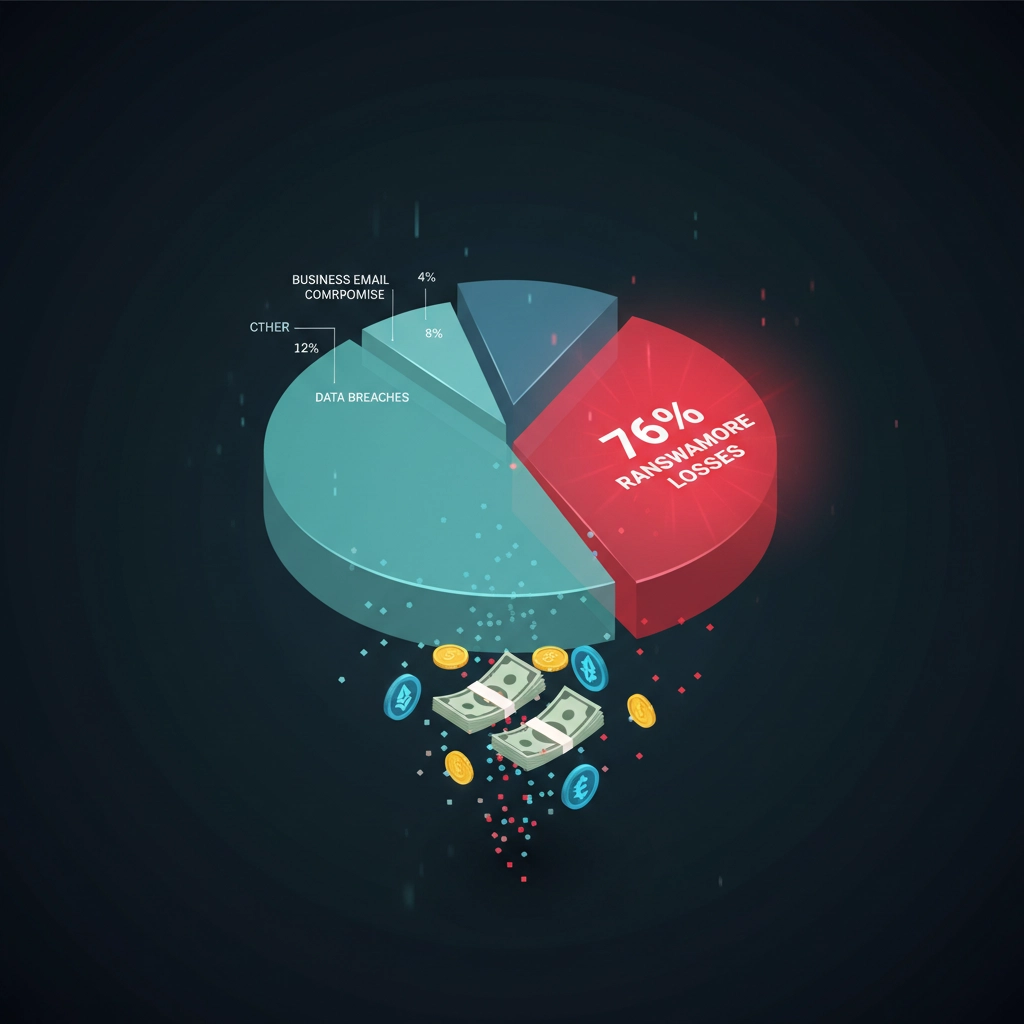
Ransomware attacks accounted for 76% of all cyber insurance losses in the first half of 2025: that's up from just 46% the year before. But here's the kicker: while ransomware only represents about 9.6% of total claims filed, these attacks are responsible for a staggering 91% of the money insurers are paying out.
Think about that for a second. Less than 10% of incidents are eating up over 90% of the payout budget.
The average ransomware attack now costs $1.18 million, up 17% from 2024. For healthcare organizations, some are facing ransom demands as high as $4 million. No wonder insurance companies are getting pickier about who they'll cover.
When you look at recovery expenses specifically, ransomware represents about 81% of claims. Translation: when businesses get hit, the cleanup costs are astronomical, and insurers are tired of footing the bill for organizations that didn't take basic precautions.
What Insurers Are Actually Asking For Now
Gone are the days of checkbox security questionnaires. In 2025, cyber insurers want documentation, proof, and evidence that you're not just another sitting duck waiting to become their next million-dollar payout.
Here's what's now considered non-negotiable for most policies:
Multi-Factor Authentication (MFA) Everywhere
Not just on your main business accounts: we're talking about MFA on every single login that touches business data. Email, cloud storage, financial systems, even your social media accounts if they're connected to your business.
Endpoint Detection and Response (EDR) Systems
Basic antivirus doesn't cut it anymore. Insurers want to see active monitoring and response capabilities on every device that connects to your network. They want logs, reports, and proof that threats are being detected and handled in real-time.
Verified Backup and Recovery Systems
This isn't just "we back up our data." Insurers now require documented testing procedures proving you can actually restore your systems. When did you last test your backups? Can you prove they work? If not, you're going to have problems.
Employee Training Documentation
Your team needs to complete cybersecurity training, and you need certificates and records to prove it. One untrained employee clicking a malicious link can trigger a million-dollar claim, so insurers want evidence your people know what they're doing.

Regular Security Assessments
Professional security reviews, vulnerability scans, and documented remediation plans. Insurers want to see that you're actively identifying and fixing security gaps, not just hoping for the best.
Tested Incident Response Plans
If something goes wrong, do you have a documented plan? Have you tested it? Can you prove it works? These aren't just nice-to-haves anymore: they're requirements.
Meeting Requirements Without Breaking the Bank
Here's the good news: implementing these controls doesn't have to cost a fortune. In fact, organizations with solid security are seeing their insurance premiums drop by 20% or more. Your security investments can actually pay for themselves.
Start with the Low-Hanging Fruit
MFA Implementation: Most of your existing systems probably already support MFA: you just need to turn it on. Microsoft 365, Google Workspace, your banking systems, and most cloud applications have built-in MFA options. Cost: Usually free or minimal monthly fees.
Employee Training: Skip the expensive consultants and use free resources from CISA, the FBI's IC3, or industry associations. Create a simple internal training program using real examples of attacks targeting businesses like yours. Document completion and test regularly.
Basic EDR Upgrade: Many antivirus vendors offer EDR capabilities as upgrades to existing licenses. Instead of switching to entirely new systems, negotiate with your current provider for enhanced monitoring and response features.
Build Documentation Systems
Create Security Logs: Start documenting everything you do for security. Every software update, every policy change, every training session. Insurers want evidence of consistent security practices, not heroic one-time efforts.
Backup Testing Schedules: Set monthly or quarterly backup restoration tests. Document the process, results, and any issues found. This proves your backups actually work when you need them.

Phase Your Investments
Quarter 1: Implement MFA, basic employee training, and documentation systems. These are the cheapest, highest-impact changes that immediately improve your insurance profile.
Quarter 2: Upgrade endpoint protection to include EDR capabilities. Negotiate with vendors for bundled services or multi-year deals to control costs.
Quarter 3: Implement formal security assessment processes. Consider using automated vulnerability scanning tools or partnering with local cybersecurity firms for periodic reviews.
Quarter 4: Develop and test comprehensive incident response plans. Use tabletop exercises to practice your response without the costs of full-scale simulations.
The Budget-Smart Approach to Vendor Selection
Bundle Services: Look for providers offering multiple security services under one contract. It's often cheaper to get MFA, EDR, and backup services from one vendor than piecing together solutions from different companies.
Leverage Local Providers: Smaller cybersecurity providers often provide more personalized service and competitive pricing compared to big-name firms. They're also more likely to work with you on payment plans or phased implementations.
Use Government Resources: Take advantage of free cybersecurity resources from CISA, the SBA, and industry associations. These organizations provide templates, training materials, and assessment tools at no cost.
Making It Work for Your Business Size
Small Businesses (1-20 employees): Focus on cloud-based solutions that don't require on-site IT management. Microsoft 365 Business Premium, Google Workspace Business Plus, or similar platforms often include many required security features in their standard packages.
Medium Businesses (21-100 employees): Consider managed security services that provide EDR monitoring and incident response without the cost of hiring dedicated security staff. Many providers offer 24/7 monitoring for less than the cost of one full-time security employee.

Growing Businesses: Implement scalable solutions that can grow with your company. Choose platforms and services that won't require complete replacement as you add employees or locations.
The Real ROI of Better Security
Organizations that invest in proper cybersecurity aren't just checking boxes for insurance: they're seeing real business benefits:
- Premium reductions of 20% or more on cyber insurance
- Higher coverage limits and better policy terms
- Reduced downtime from security incidents
- Better customer trust and competitive advantages
- Compliance with data protection regulations
Your Next Steps
The cyber insurance market has fundamentally changed, and there's no going back to the "good old days" of easy coverage. But this shift isn't necessarily bad news: it's forcing businesses to implement security measures they should have had all along.
Start with a simple assessment: which of the required controls do you already have in place? What's missing? What can you implement quickly and inexpensively?
Don't wait until renewal time to address these requirements. Insurance applications now take longer to process, and coverage gaps can leave your business exposed to devastating financial losses.
The businesses that adapt quickly to these new requirements won't just secure better insurance terms: they'll build more resilient operations that can withstand the evolving threat landscape. And in 2025, that's not just smart business: it's essential survival.
Ready to get your cybersecurity house in order without breaking your budget? Contact B&R Computers to discuss a practical, phased approach to meeting your cyber insurance requirements while building real security for your business.




































































































