Picture this: It's 3 PM on a Tuesday, and your phone rings. Your accounting software vendor is calling to inform you they've been hacked. Your heart sinks as you realize that all your financial data, customer information, and business records might be at risk. Sound scary? It should – because vendor breaches are becoming the #1 way cybercriminals are infiltrating small businesses in 2025.
Here's the reality check: When your vendor gets compromised, you don't have hours to figure out your response. You have minutes. The good news? With the right checklist, you can protect your business even when your vendors fail you.
The Critical 5-Minute Response Checklist
When you get that dreaded breach notification call, every second counts. Here's exactly what you need to do, step by step:
Minutes 1-2: Emergency Lockdown
Step 1: Cut all vendor access immediately. This isn't the time to be polite or worry about hurting feelings. Disable their VPN access, revoke user privileges, change any shared passwords, and shut down every system connected to that vendor. Even if they swear the breach is "contained," assume it isn't.
Step 2: Alert your core team. Send a quick message to your key staff members: "Vendor [Name] breach – emergency response activated. All hands on deck." Don't go into details over unsecured channels yet.

Minutes 2-4: System Assessment
Step 3: Check your network logs. Look for any unusual activity, especially around the times your compromised vendor had access to your systems. If you don't have someone who can do this quickly, this is where having a cybersecurity partner like B&R Computers becomes invaluable.
Step 4: Review what data was exposed. Make a quick list of what information the vendor had access to – customer data, financial records, employee information, or proprietary business data. You'll need this for the next steps.
Step 5: Test your network segmentation. Can the breach spread to other parts of your business? If your network isn't properly segmented (most small businesses aren't), assume the worst and prepare for a broader incident response.
Minute 5: Documentation and Initial Communication
Step 6: Start documenting everything. Write down the time you were notified, what the vendor told you, and every action you've taken. This documentation will be crucial for insurance claims and regulatory compliance.
Step 7: Prepare your communication plan. You'll need to notify customers, employees, and potentially regulators. Don't send anything yet – just prepare your key messages.
Real-World Wake-Up Calls
Think vendor breaches are rare? Think again. Remember when Kaseya, a managed service provider used by thousands of small businesses, got hit with ransomware in 2021? Over 1,500 companies were affected downstream. Or when SolarWinds was compromised, affecting 18,000+ organizations who thought they were just getting routine software updates.
The scary part? Most small businesses never even knew they were at risk until it was too late. They trusted their vendors completely and had no backup plan when that trust was betrayed.

One of our clients, a local manufacturing company, learned this lesson the hard way. Their payroll provider was breached, exposing every employee's personal information, Social Security numbers, and bank details. Because they had followed a response plan similar to this checklist, they contained the damage within hours instead of days. The difference? They kept their reputation intact and avoided costly regulatory fines.
Beyond the 5 Minutes: Your Extended Response Plan
Once you've completed your emergency response, here's what comes next:
Immediate Actions (Next 24 Hours)
Conduct a full security audit. Go beyond just checking for immediate threats. Look at your entire vendor ecosystem and identify other potential vulnerabilities. If one vendor got compromised, others might be at risk too.
Engage with cybersecurity experts. Unless you have dedicated IT security staff, you'll need professional help to assess the full impact and ensure you haven't missed anything critical.
Notify relevant parties. Depending on your industry and the type of data involved, you may need to notify customers, regulatory bodies, or law enforcement. Each has different timing requirements, so don't delay.
Week 1-2: Investigation and Recovery
Work with the vendor on incident details. Once you've secured your own systems, work with your vendor to understand exactly what happened, what data was affected, and what they're doing to prevent future breaches.
Review and update access controls. This is the perfect time to implement stronger authentication requirements for all vendor access, including multi-factor authentication and regular access reviews.
Consider cyber insurance claims. If you have cyber liability insurance, start the claims process early. The documentation you started during your 5-minute response will be invaluable here.
Building Long-Term Vendor Security
The best defense against vendor breaches is prevention. Here's how to protect yourself before the next call comes in:
Vendor Risk Assessment
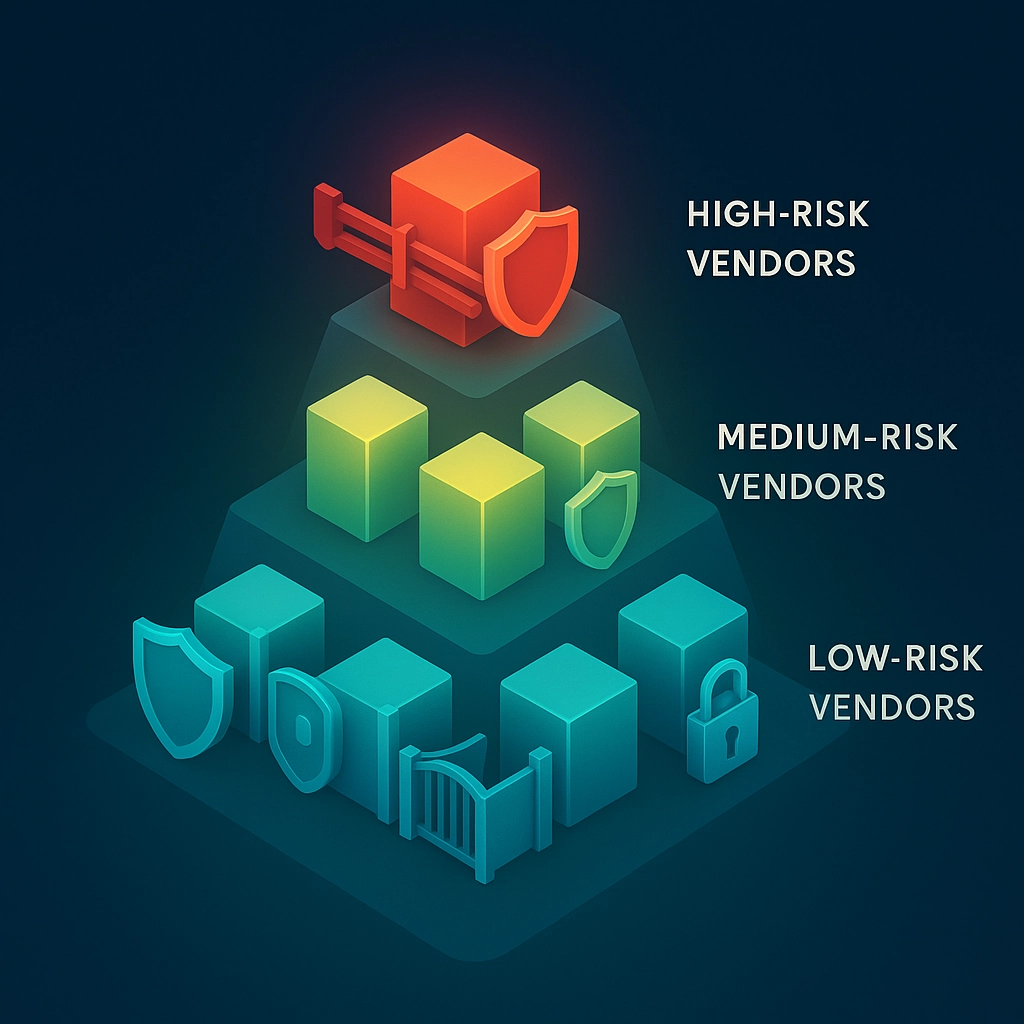
Not all vendors are created equal. Your email provider has different risk levels than your office supply company. Classify your vendors into three categories:
- High Risk: Access to sensitive data or critical systems
- Medium Risk: Limited access but still important to operations
- Low Risk: Minimal access and easily replaceable
Contract Protection
Your vendor contracts should include specific cybersecurity requirements, including:
- Mandatory breach notification within 24 hours
- Regular security audits and certifications
- Cyber insurance requirements
- Clear liability terms for data breaches
Ongoing Monitoring
Don't wait for vendors to tell you they've been compromised. Monitor vendor security continuously through:
- Regular security questionnaires
- Third-party risk assessment tools
- News monitoring for vendor security incidents
- Annual security reviews for high-risk vendors
The Network Segmentation Safety Net
Here's a truth bomb: If a vendor breach can take down your entire business, your network security architecture is fundamentally flawed. Proper network segmentation means that even if one part gets compromised, the rest of your business keeps running.
Think of it like compartments on a ship. If one compartment floods, the ship doesn't sink because the other compartments remain watertight. Your business network should work the same way.
Don't Go It Alone
Managing vendor cybersecurity risks isn't a part-time job you can handle between running your business and everything else on your plate. The threats are too sophisticated, and the stakes are too high.
The most successful small businesses we work with have learned to treat cybersecurity like any other critical business function – something that requires professional expertise and ongoing attention. They don't try to become cybersecurity experts themselves; they partner with professionals who live and breathe this stuff every day.
Your Next Steps
Vendor breaches aren't a matter of if, but when. The businesses that survive and thrive are the ones that prepare before disaster strikes, not after.
Start by taking inventory of your current vendors and their access to your systems. Then, implement the emergency response checklist we've outlined here. Most importantly, don't wait until you're in crisis mode to figure out your cybersecurity strategy.
Ready to bulletproof your business against vendor security risks? At B&R Computers, we help small businesses build comprehensive cybersecurity strategies that protect against vendor breaches and other evolving threats. We'll work with you to assess your vendor risks, implement proper network segmentation, and create response plans that actually work when you need them most.
Contact us today to schedule a vendor risk assessment and discover how we can help protect your business from the cybersecurity risks hiding in your supply chain. Because when your vendor calls with bad news, you'll be ready.




































































































