That trusty desktop computer from 2018 is still chugging along fine, right? Your network router hasn't given you trouble in years, and those old laptops work perfectly for basic tasks. But here's the uncomfortable truth: your aging hardware might be silently undermining your entire security strategy.
Companies using outdated systems are 53% more likely to suffer data breaches, and a staggering 68% of all data breaches are linked to vulnerabilities in outdated systems. Your old hardware isn't just slowing you down: it's creating an open door for cybercriminals.
The Hidden Dangers Lurking in Legacy Hardware
When manufacturers stop supporting hardware, they stop releasing security patches. It's that simple. Your five-year-old router might seem fine, but if the manufacturer declared it "end-of-life" last year, every security vulnerability discovered since then remains unpatched and exploitable.
Think of it this way: imagine leaving your office door unlocked because the lock manufacturer stopped making keys. That's essentially what happens when hardware reaches end-of-life status. The device keeps working, but the security mechanisms become frozen in time while threats continue evolving.
Here's what makes this particularly dangerous for businesses:
Unpatched vulnerabilities stack up over time. Each month without security updates adds new potential entry points for attackers. What starts as one small vulnerability can quickly become dozens of exploitable weaknesses.
Old hardware can't run modern security software. Your 2019 laptop might struggle to run current endpoint protection tools effectively, creating gaps in your defense coverage that you might not even realize exist.
Compliance becomes impossible. Many industry standards require current, supported systems. Using unsupported hardware can put you out of compliance with regulations that affect your contracts and customer relationships.
Warning Signs Your Hardware Needs Attention
Not sure if your equipment has crossed the line from "vintage" to "vulnerable"? Here are the red flags every business owner should watch for:
Your software is stuck in the past. If you can't upgrade to the latest versions of essential software because your hardware won't support it, you're in dangerous territory. Outdated software means missing critical security patches.
Performance has noticeably declined. Frequent crashes, slow startup times, and random freezes aren't just productivity killers: they're often signs that hardware is failing in ways that could compromise security.
The manufacturer website doesn't mention your model anymore. If you have to scroll through "legacy products" or "discontinued items" to find your device, it's time to start planning its replacement.

Your IT person sighs when you mention certain equipment. Trust their instincts. If maintaining a piece of hardware requires creative workarounds and prayers, it's probably creating security risks.
The Replace vs. Retire vs. Reinforce Decision
Not every piece of aging hardware needs the same approach. Here's how to decide what to do with each device:
When to Replace
Security support has ended. This is non-negotiable. When manufacturers stop providing security updates, replacement is your only safe option. No amount of additional security software can compensate for fundamentally unpatched hardware.
The device has been compromised. If a piece of equipment has been infected or hacked, replacement prevents the infection from spreading and ensures you're starting with a clean slate.
Downtime costs exceed replacement costs. When you're spending more on repairs and lost productivity than a new device would cost, the math is clear.
When to Retire
Some older hardware can be safely taken out of service without replacement:
Redundant systems that created security complexity. That backup server you never use might be creating more risk than value. Fewer systems mean fewer potential entry points.
Single-purpose devices that aren't business-critical. Old printers, scanners, or specialty equipment that's used occasionally might not justify the security risk.
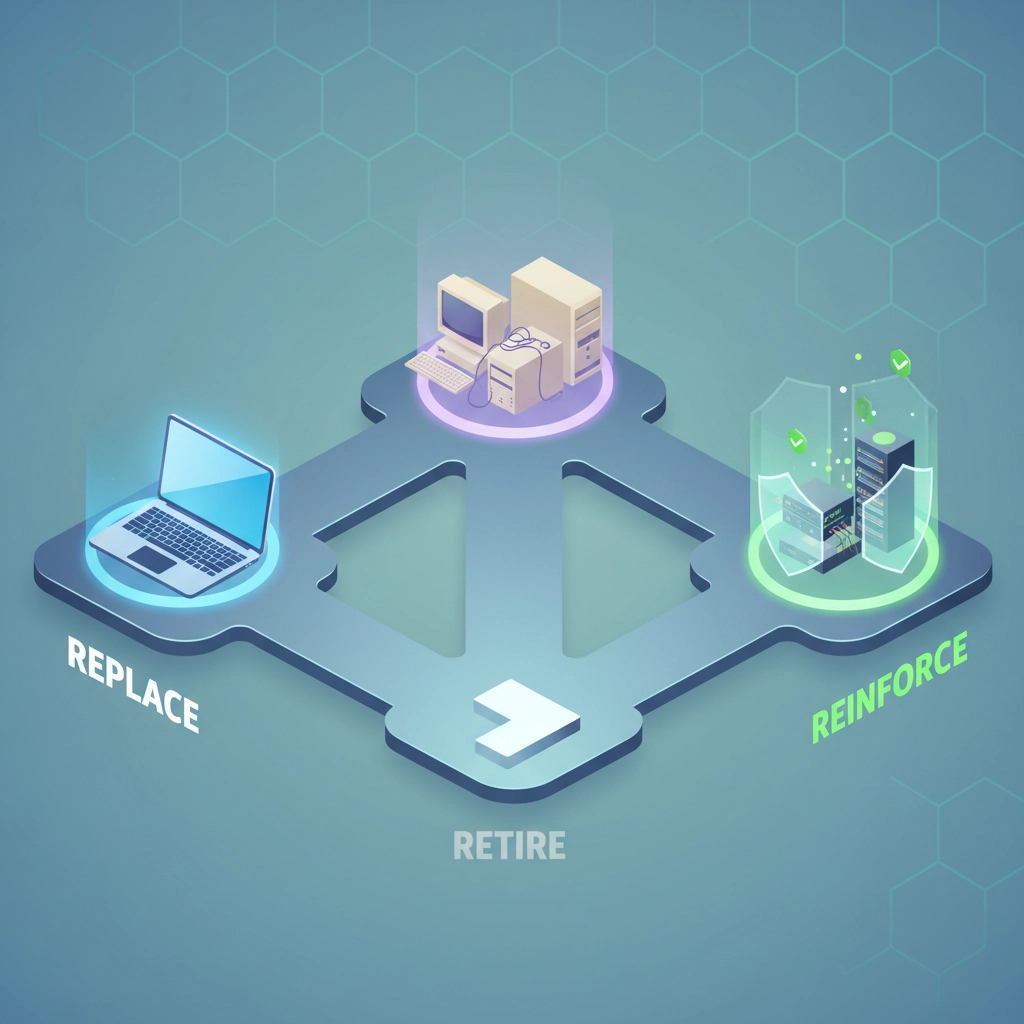
When to Reinforce (Carefully)
In limited situations, you might keep older hardware with additional protections:
Air-gapped systems. Equipment that's completely isolated from your network and the internet poses minimal security risk, even when old.
Hardware that's still supported but aging. If the manufacturer still provides security updates, additional monitoring and endpoint protection can extend safe usage.
Equipment with planned replacement dates. If you're already budgeting for replacement within six months, temporary additional security measures might bridge the gap safely.
The Real Cost of Waiting
Many business owners delay hardware upgrades because they see them as expenses rather than investments. But consider the true cost of a security breach caused by outdated hardware:
The average data breach costs small businesses $108,000, and that's just the immediate financial impact. Add in lost customer trust, regulatory fines, and business disruption, and the total cost often reaches multiple times the original figure.
Meanwhile, proactive hardware replacement offers measurable benefits beyond security. Modern equipment runs more efficiently, supports better productivity tools, and often reduces energy costs. Your team spends less time waiting for slow systems and more time doing valuable work.
Making Smart Hardware Decisions
Ready to assess your current setup? Start with these practical steps:
Create a hardware inventory with purchase dates and support status. You can't protect what you don't know about. List every device connected to your network along with when support ends.
Prioritize based on risk and business impact. Focus first on internet-connected devices and those handling sensitive data. A compromised email server poses more risk than an offline backup drive.
Budget for replacement cycles, not emergency purchases. Plan to replace computers every 3-4 years, network equipment every 5-6 years, and servers every 4-5 years. Scheduled replacements cost less than emergency ones.

Work with qualified professionals for disposal. Don't just throw old hardware in the dumpster. Proper data destruction and recycling protect both your information and the environment.
Your Next Steps
The good news? You don't have to replace everything at once. Start by identifying your highest-risk devices: typically internet-connected equipment that's no longer supported by the manufacturer. Create a replacement schedule that spreads costs over time while addressing the most dangerous vulnerabilities first.
Remember, every month you delay gives potential attackers more time to discover and exploit vulnerabilities in your aging systems. The question isn't whether old hardware creates security risks: it's how long you're willing to leave your business exposed.
Ready to assess your hardware security risks and create a smart replacement strategy? Our team specializes in helping businesses identify vulnerable equipment and plan cost-effective upgrades that actually improve both security and productivity. Contact B&R Computers today for a comprehensive hardware security assessment.
Your business deserves technology that protects rather than threatens your success. Don't let aging hardware become the weak link that compromises everything you've built.




































































































