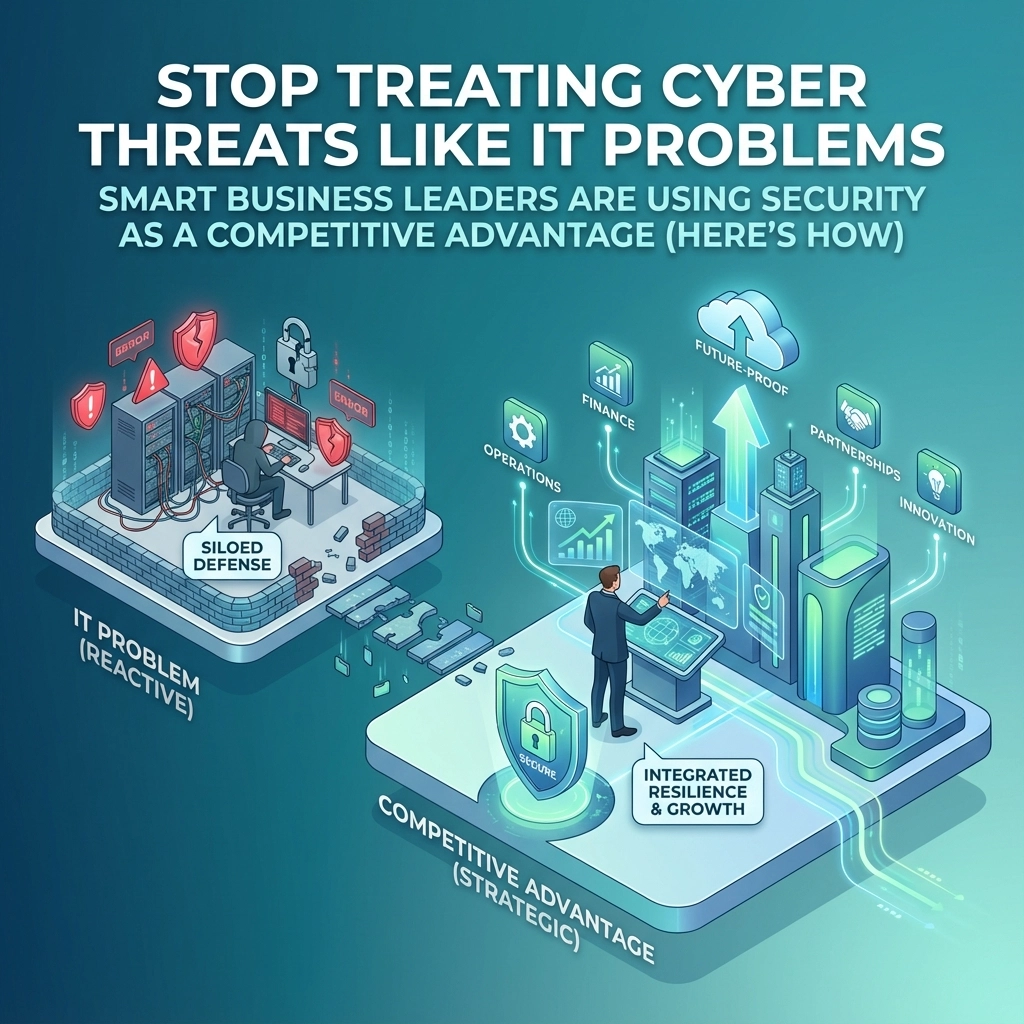
Here's the uncomfortable truth most business owners don't want to hear: while you've been treating cybersecurity as an expensive IT headache, your smartest competitors have been turning it into their secret weapon.
The old playbook of viewing security as a necessary evil: something you grudgingly spend money on to avoid getting hacked: is not just outdated. It's actively hurting your business. In 2025, the companies winning new clients, charging premium prices, and building unshakeable customer loyalty are the ones who've figured out something crucial: cybersecurity isn't a cost center. It's a profit center.
The 2025 Reality: Security as a Client Magnet
The numbers don't lie. Recent research shows that 64% of C-suite executives now view cybersecurity as a significant competitive advantage, not just a defensive measure. But here's what's really eye-opening: 41% of customers say they actively trust businesses with robust cybersecurity more than their competitors, and 83% are willing to share their data: and their business: with companies they trust to protect it.
This isn't theoretical anymore. Companies with demonstrable security excellence are seeing 12% lower customer churn rates and can close enterprise deals 22% faster than competitors without strong security credentials. When the average data breach costs $4.88 million, preventing one doesn't just save money: it preserves the trust that took years to build.

But the real shift happening in 2025 goes deeper than risk prevention. Smart business leaders are discovering that cybersecurity excellence opens doors that traditional marketing and sales tactics simply can't.
How Local Businesses Are Leading the Charge
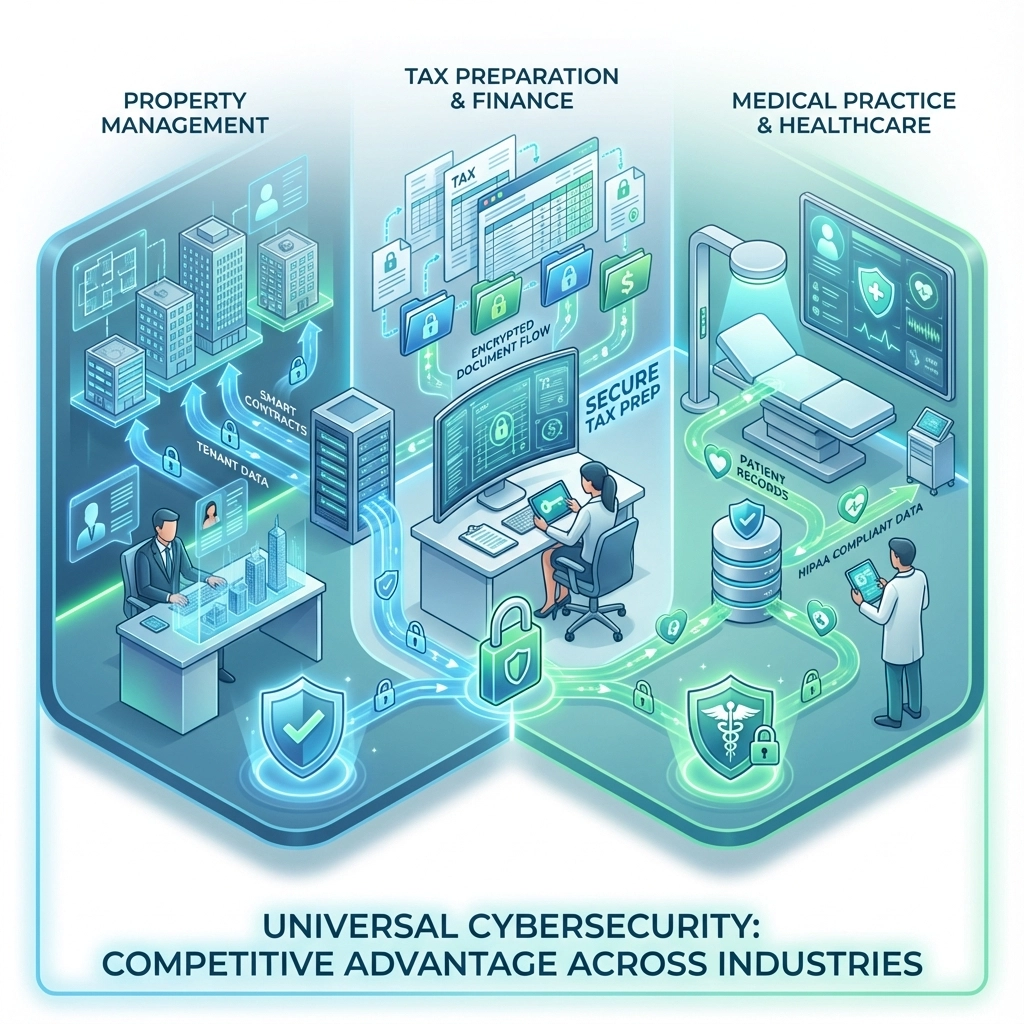
Property Management: From Liability to Selling Point
Take Sarah Chen, who runs a 400-unit property management company in Richmond. Two years ago, she viewed cybersecurity as another compliance burden: something needed to protect tenant data and avoid lawsuits. Then she started marketing her security certifications to potential clients.
"Property owners began choosing us specifically because we could prove their tenants' financial information was protected," Chen explains. "We went from competing on price to competing on trust. Our client acquisition costs dropped 30% because word-of-mouth referrals exploded."
Chen now includes her security audit reports in sales presentations. Property owners see her investment in cybersecurity as evidence that she'll protect their investment with the same diligence.
Tax and Financial Services: Security as Premium Positioning
Mike Rodriguez runs a mid-size accounting firm that specializes in small business tax preparation. After implementing comprehensive cybersecurity measures including encrypted client portals and advanced threat detection, he made a strategic decision: he started charging 20% more than local competitors.
"At first, I thought clients would balk at the higher fees," Rodriguez says. "Instead, they thanked me. They'd heard too many horror stories about tax firms getting breached right before filing season. Our security investment became our biggest differentiator."
His firm now markets itself as "the secure choice for business tax preparation" and maintains a waiting list during tax season. Clients pay more because they value the peace of mind.
Healthcare: Security Driving Patient Loyalty
Dr. Amanda Foster's family practice implemented Zero Trust security architecture after a nearby clinic suffered a ransomware attack that shut them down for three weeks. But instead of keeping the investment quiet, she made it part of her patient communication strategy.
"We put up signs explaining our security measures, sent letters to patients about our data protection commitment, and trained staff to explain why we ask for ID verification," Foster explains. "Patient retention improved dramatically. People started referring friends specifically because they felt their medical information was truly safe with us."
The Four Pillars of Security-Driven Competitive Advantage
1. Trust-Based Premium Pricing
Companies with verifiable security excellence can charge 15-25% more for the same services. Clients understand they're paying for protection, reliability, and professionalism that extends beyond the core service.
2. Accelerated Sales Cycles
When prospects see security certifications, audit reports, and clear data protection policies, objections around trust and reliability disappear. Enterprise clients especially move faster when they don't have to worry about vendor risk assessments.
3. Word-of-Mouth Multiplication
Nothing spreads faster than recommendations from clients who feel genuinely protected. Security-focused businesses report 40-60% higher referral rates because satisfied clients become active advocates.
4. Partnership Opportunities
Other businesses actively seek partnerships with security-conscious companies. Banks, law firms, and healthcare organizations prefer vendors who won't create compliance headaches or reputational risks.
Making the Mindset Shift: From Expense to Investment
The transition from viewing cybersecurity as an IT problem to leveraging it as a business advantage requires three fundamental changes:
Strategic Integration, Not Tactical Patching
Stop thinking about cybersecurity as something that happens after business decisions are made. Instead, build security considerations into every client interaction, every process improvement, and every growth initiative. When security becomes part of your business DNA, clients notice.
Transparency as Differentiation
Most businesses hide their security investments, treating them as background necessities. Smart leaders do the opposite: they showcase their security measures as evidence of their commitment to client protection and business excellence.

Proactive Communication
Don't wait for clients to ask about your security measures. Include them in proposals, feature them on your website, and train your team to discuss them confidently. When a prospect asks, "How do you protect our data?" your answer should sound like a competitive advantage, not a compliance checklist.
The 2025 Trends Making This Shift Essential
Several converging trends are making security-driven differentiation not just possible, but necessary:
Regulatory Scrutiny: New compliance requirements mean businesses need partners who won't create regulatory headaches.
Vendor Risk Assessments: Companies are increasingly evaluating the security posture of every vendor before signing contracts.
Insurance Requirements: Business insurance policies now include cybersecurity requirements that affect coverage and rates.
Client Education: Business owners now understand cybersecurity risks well enough to make vendor decisions based on security capabilities.
The Practical Next Steps
The companies winning with security-as-advantage aren't necessarily spending more on cybersecurity: they're spending smarter and communicating better.
Start by documenting your current security measures. Most small businesses have more protections than they realize; they just don't know how to talk about them strategically.
Next, identify which of your security investments could become selling points. If you've implemented multi-factor authentication, encryption, or regular security training, these aren't just protective measures: they're proof points of your commitment to client protection.
Finally, train your team to discuss security confidently during client interactions. When someone asks about data protection, your response should reinforce why working with you is the smart, safe choice.
The businesses thriving in 2025 understand that in a world where trust is increasingly rare, demonstrable security excellence isn't just a defensive necessity: it's their most powerful competitive weapon.
Ready to discover how your current security investments could become your biggest competitive advantages? Let's schedule a complimentary security posture review with B&R Computers. We'll help you identify which of your existing protections could be driving new business: and what strategic additions could set you apart from every competitor in your market.