The ransomware game just changed: permanently. While you were focusing on traditional security threats, cybercriminal organizations quietly transformed from scattered gangs into sophisticated cartels with AI-powered arsenals. These aren't the same hackers from 2023 working alone in basements. We're now dealing with coordinated super groups that share resources, pool expertise, and deploy artificial intelligence to accelerate every phase of their attacks.
The numbers tell the story: ransomware attacks surged 126% between January and September 2025, with October alone recording 623 incidents: a 30% monthly increase. More alarming? Attackers' "breakout time" (the window between initial access and spreading through your network) collapsed from 48 minutes to just 18 minutes this year.
For small business owners, this isn't just another cybersecurity headline to scroll past. These AI-powered super gangs are specifically targeting SMBs because you're seen as easier prey with valuable data and limited security resources. Here's what's really happening and how to protect your business.
The Cartel Model: How Ransomware Became Big Business
Forget everything you thought you knew about ransomware groups. The biggest transformation isn't technological: it's organizational. Criminal groups are now operating like legitimate corporations, complete with franchising models, brand licensing, and strategic partnerships.
DragonForce pioneered what security researchers call the "ransomware cartel model." Instead of each group working independently, they created a white-label system where affiliates operate semi-independently using shared infrastructure, tooling, and unified branding. Think of it as franchising, but for cybercrime.

This model spreads risk while dramatically expanding reach. DragonForce has since formed partnerships with established groups like Qilin and LockBit, facilitating shared attack techniques, resources, and infrastructure. Meanwhile, other major players formed direct alliances: Scattered Spider, LAPSUS$, and ShinyHunters united as "Scattered LAPSUS$ Hunters," with each group specializing in different attack phases.
This isn't just criminal cooperation; it's criminal evolution. By pooling resources and expertise, these super gangs can target more businesses simultaneously while reducing individual group exposure to law enforcement.
AI: From Experiment to Weapon
Here's what keeps security experts awake at night: these groups aren't experimenting with AI anymore: they're using it operationally across every attack phase. The impact on attack speed and sophistication is measurable and terrifying.
Current AI capabilities being deployed include:
Hyper-Realistic Social Engineering: AI generates phishing emails, phone scripts, and even voice synthesis that adapts local accents and dialects. Your employees can't distinguish these from legitimate communications.
Evasion Automation: AI automatically obfuscates malicious code, kills antivirus software, and adapts attack methods in real-time when detection systems activate.
Victim Profiling: AI analyzes your business's digital footprint to craft personalized attacks targeting specific employees, vendors, or business processes.
Negotiation Enhancement: AI assists in extortion tactics, analyzing victim responses to optimize ransom demands and payment pressure.
The speed advantage is crushing traditional defenses. When attackers can move from initial compromise to full network control in under 20 minutes, most small businesses don't have time to detect, let alone respond to, the threat.
Why Small Businesses Are Prime Targets
These super gangs aren't just more sophisticated: they're more strategic about target selection. Small businesses represent the perfect storm of valuable data, limited security resources, and faster time-to-payment.
Your business likely stores customer data, financial records, and operational information that's extremely valuable on dark web markets. Unlike large corporations with dedicated security teams, you probably rely on basic antivirus software and hope for the best. When ransomware hits, you're more likely to pay quickly rather than endure weeks of downtime and investigation.
The cartel model makes this targeting even more efficient. Different groups can specialize: one focuses on initial access through social engineering, another handles lateral movement and data exfiltration, and a third manages the encryption and extortion phases.
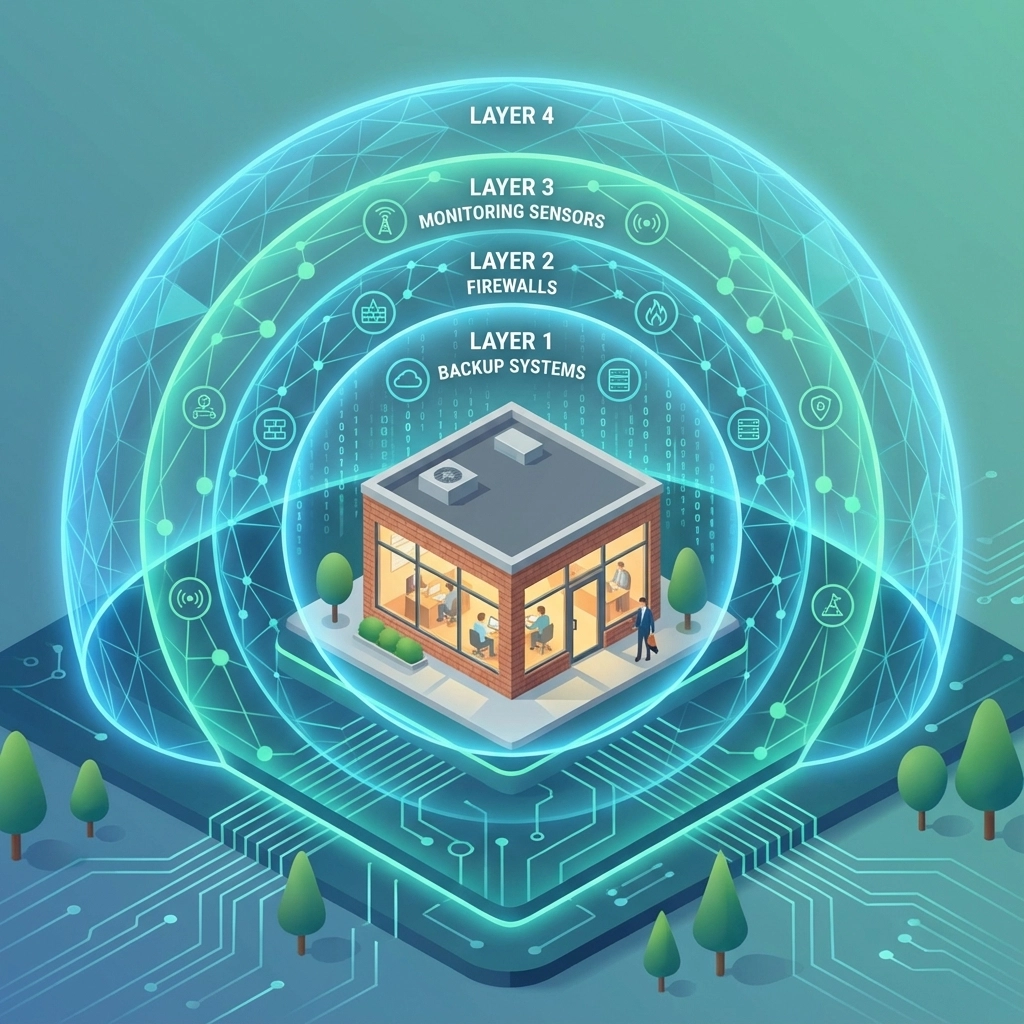
The 4-Layer Defense Framework That Actually Works
Traditional security advice tells you to "keep software updated" and "train your employees." That's not enough anymore. You need a modern defense framework designed specifically for the AI-powered cartel threat.
Layer 1: Connected Security Architecture
Your security tools must communicate with each other. Isolated antivirus software, standalone firewalls, and disconnected backup systems create blind spots that AI-powered attacks exploit.
Implement unified threat detection that connects your endpoint protection, network monitoring, and identity management systems. When one system detects suspicious activity, all others should automatically adjust their defensive posture.
For small businesses, this means choosing security vendors that offer integrated platforms rather than cobbling together multiple point solutions. The extra cost is far less than recovering from a successful ransomware attack.
Layer 2: Anti-Phishing at Scale
Since voice phishing and targeted social engineering are now primary entry vectors, you need defenses that go beyond traditional email filters.
Deploy email security solutions with behavioral analytics capable of detecting AI-generated content. But don't stop there: implement mandatory security awareness training that specifically covers voice phishing, vendor impersonation, and urgent request scenarios.
Create verification procedures for any financial requests, password resets, or system changes: even when they appear to come from trusted sources. AI-generated communications are becoming indistinguishable from legitimate ones, so process verification matters more than content analysis.
Layer 3: Early Detection and Deception
With only 18 minutes between initial compromise and network spread, detection speed is everything. Traditional antivirus software that waits for known signatures won't save you.
Implement behavioral monitoring that identifies unusual file access patterns, unauthorized network communications, and suspicious administrative activity. Consider deception technology: fake files and network assets that trigger immediate alerts when accessed.
For small businesses, this might mean managed detection and response (MDR) services that provide 24/7 monitoring without the overhead of building an internal security operations center.
Layer 4: Backup Resilience and Recovery
Your backup strategy must assume that attackers will find and encrypt your primary backup systems. Modern ransomware specifically targets backup infrastructure to eliminate recovery options.
Maintain offline, air-gapped backups stored separately from your primary network. Test recovery procedures monthly, not annually. Many businesses discover their backups are corrupted or incomplete only after an attack occurs.
Implement backup versioning that preserves multiple restoration points. If ransomware encrypts files gradually over weeks before revealing itself, you need clean versions from before the initial compromise.
Implementation Reality Check
This framework isn't theoretical: it's what works against current threats. But implementation requires honest assessment of your current security posture and realistic budgeting for modern protection.

Start with Layer 2 (anti-phishing) since social engineering remains the primary attack vector. Most successful ransomware attacks begin with a convincing email or phone call that tricks an employee into providing access.
Layer 3 (detection) provides the biggest impact for small businesses, since speed advantages can neutralize even sophisticated attacks if you catch them early enough.
Layers 1 and 4 require more planning and investment but provide the foundational security that makes other layers effective.
The Bottom Line for Small Business Owners
The ransomware threat has fundamentally evolved beyond what traditional security approaches can handle. AI-powered super gangs aren't coming: they're already here, and they're specifically targeting businesses like yours.
But this isn't a doomsday scenario. Businesses that implement modern, layered defenses are successfully repelling these advanced attacks. The key is understanding that cybersecurity isn't a technology problem: it's a business continuity issue that requires appropriate investment and strategic thinking.
The cost of implementing proper defenses is significant, but it's fractional compared to the average $1.85 million cost of a successful ransomware attack on a small business. More importantly, many businesses never recover from the operational disruption and reputation damage.
Ready to assess your current security posture against these evolving threats? Contact our cybersecurity experts for a comprehensive evaluation of your defenses and a customized implementation plan for the 4-layer framework. Your business's survival might depend on the actions you take today.





































































































